Payment scams and cybersecurity
Paying online by card is convenient and quick. So is using online banking - that is, making transfers and other transactions through your bank's website or app. But is it safe? Yes, provided you follow a few simple precautions that protect you from fraud. Your caution, combined with the security technology behind digital payments, makes it harder for criminals to succeed. Moreover, if you do fall victim to fraud and have acted diligently, you are protected and can request reimbursement of the stolen funds.
Let's explore how online payment scams work, what technology safeguards you, how to protect yourself, and what to do if a fraudster still manages to cause you harm.
How online payment scams work
You can fall victim to fraud in three ways, depending on whether the fraudster:
- issues a payment order directly (for example, a credit card payment) after illegally obtaining your credentials or confidential information (such as your card number);
- modifies a legitimate payment order by intercepting electronic communication between your device and the recipient's-for example, via malware or cyberattacks;
- manipulates you into making a payment to them, for example by telling you a family member is in trouble and needs money.
Let's examine these types of fraud in more detail.
A fraudster can use various methods to obtain your details and directly issue payment orders.
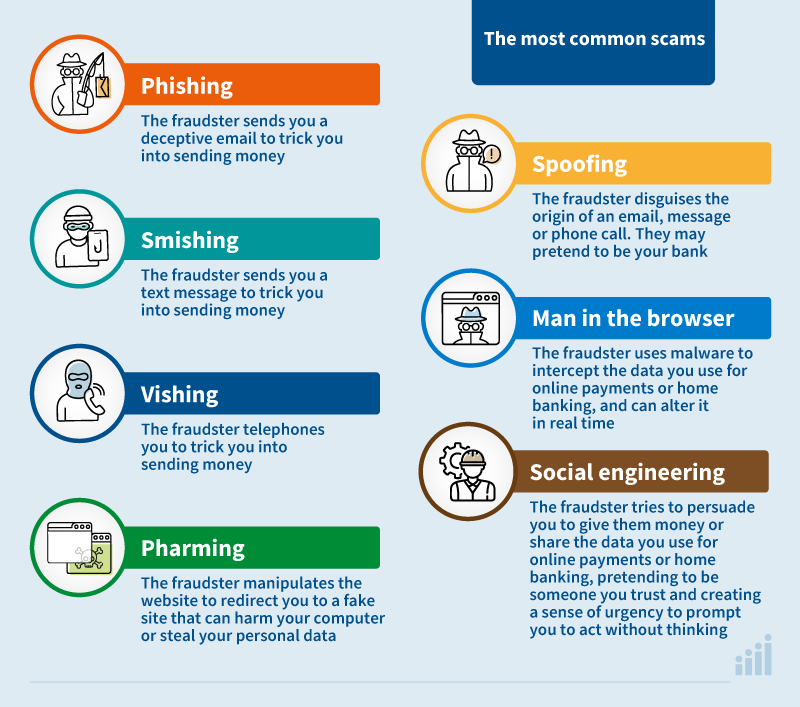
- Phishing. The fraudster sends you a deceptive email to trick you into sending money, revealing your card or online banking details, or downloading malware (a virus that infects your device). They often ask you to click a link or scan a QR code in the email; if you do, the link may take you to a fake website where you enter confidential details (which the fraudster steals) or cause malware to be downloaded. Whatever the scammer asks, they usually create a sense of urgency to prompt impulsive action. Phishing emails may be sent randomly to many people hoping some will take the bait (phishing is a play on “fishing”), or targeted at specific individuals or organisations.
- Smishing. Works like phishing but uses text messages to your phone instead of emails.
- Vishing. Works like phishing but involves phone calls instead of emails.
- Pharming. A technique that redirects you to fake websites closely resembling official ones - such as your bank's site - to trick you into entering credentials or sensitive data that the fraudster intercepts and steals.
Fraudsters often combine these methods with spoofing, which disguises the origin of the email, message, or call. For example, posing as your bank, they make the sender's email address or phone number appear genuine. Spoofing makes phishing and its variants even more insidious.
Important!
Your bank will never ask for your online banking or payment details by email or phone. If you receive such a request, ignore it - it is a scam!
To alter payment data, fraudsters may use other tactics, such as the so-called man-in-the-browser scam. This intercepts payment data you enter online or via online banking and modifies legitimate payment orders in real time, diverting funds to the fraudster's account. They use malware embedded in your web browser (the programme you use to surf the internet) that can change payment details or web pages as you view them-for example, switching the recipient or amount when you make an online transfer.
Sometimes, the fraudster tries to persuade you to hand over money or payment credentials (social engineering): they may pretend to be someone you trust, such as a relative, your bank, a public authority, or a company you deal with; promise something positive like a prize or refund, or threaten something negative like a fine or card suspension; or create urgency, for example imposing a deadline, to pressure you into complying without thinking. This is the most insidious type of fraud because it bypasses security systems - you yourself authorise the transaction.
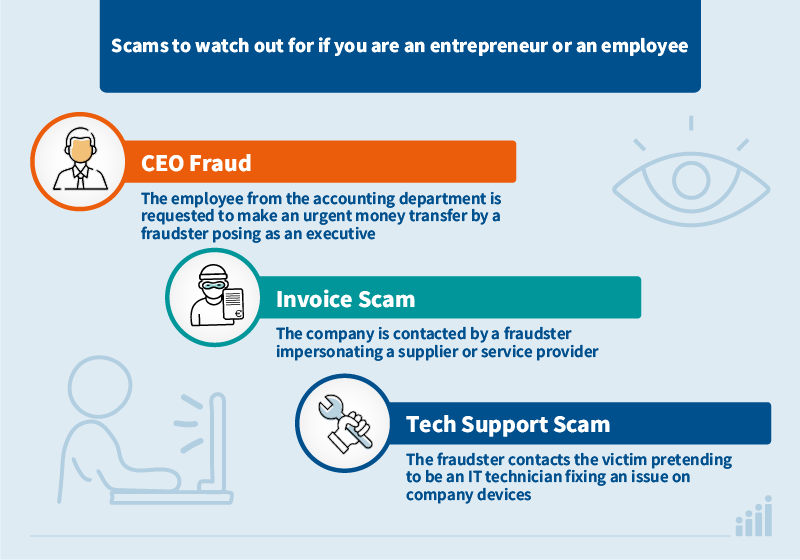
Even at work, you can fall victim to social engineering scams, for example when:
- fraudsters pose as executives and send apparently legitimate emails to the accounting department requesting urgent money transfers (CEO fraud);
- fraudsters impersonate energy suppliers and contact the company by phone or email, asking to change bank details for invoice payments or sending invoices with new bank details (invoice scam);
- fraudsters call or email pretending to be technicians fixing issues on company devices and convince employees to install remote access software which they use to steal data or install malware (tech support scam).
In In practice, the boundaries between scam types are not always clear, and fraudsters often combine tactics: for example, calling you (vishing) and persuading you (social engineering) to click a link that installs malware without your knowledge.
The technology that protects you
If you pay online or use online banking, you already benefit from this technology: it is called strong customer authentication. You authenticate yourself by proving that it is really you making the payment with your card or accessing your account. Previously, a single proof, such as entering a password, was enough; now you need at least two of the following:
- knowledge (something only you know, like a password);
- possession (something only you have, like your phone);
- inherence (something inherent to you, like your fingerprint).
That's why, for example, when you shop online with your card, you may be asked to enter a PIN (something you know) and then a code sent to your phone (something you have).
Risks
Because of scams, when you pay online you risk losing money or confidential data. To protect yourself, prudence is essential. Two-factor authentication is effective but only half of your defence; the other half is how you behave. If someone convinces you to make a payment in their favour, strong authentication won't help because you've bypassed the security checks yourself.
Follow these tips to minimise the risk.

What to do if you've been scammed
If a fraudster has taken money - by using your card or making a transfer from your online account - it's not all lost: you can dispute the transactions and seek reimbursement. Follow these steps:
- report the fraudulent transactions to your bank immediately and request a refund;
- if the bank refuses reimbursement and you believe you acted correctly, you can submit a written dispute;
- if the bank denies your refund request or fails to respond to your dispute notification within 15 working days, you may also submit a complaint directly to the Banking and Financial Ombudsman (ABF);
- in any case you can file a complaint with Banca d'Italia.
Filing a police report is not required to get reimbursed, but it helps fight fraud.
Important!
You are entitled to a refund only if you acted diligently - that is, you followed recommended precautions. You generally lose this right if you gave your credentials over the phone to a fraudster or if your wallet containing card and PIN was stolen.
Regarding the ABF appeal, note that payments you authorised (for example, purchases from sellers who turned out to be fraudulent) are excluded.
Would you like to learn more about protecting yourself from online payment fraud? Read the Banca d'Italia's Guide on e-commerce payments, watch the webserie 'I Navigati' (only in Italian) and the videos from 'Cybersicuri - Impresa possibile' (only in Italian).






 Youtube
Youtube
 X - Banca d’Italia
X - Banca d’Italia
 Linkedin
Linkedin
 RSS
RSS